How secure is your company with respect to its wireless network?
Important information may be leaking through your network right now
AtEar provides an integrated solution to securely manage your wireless network
.
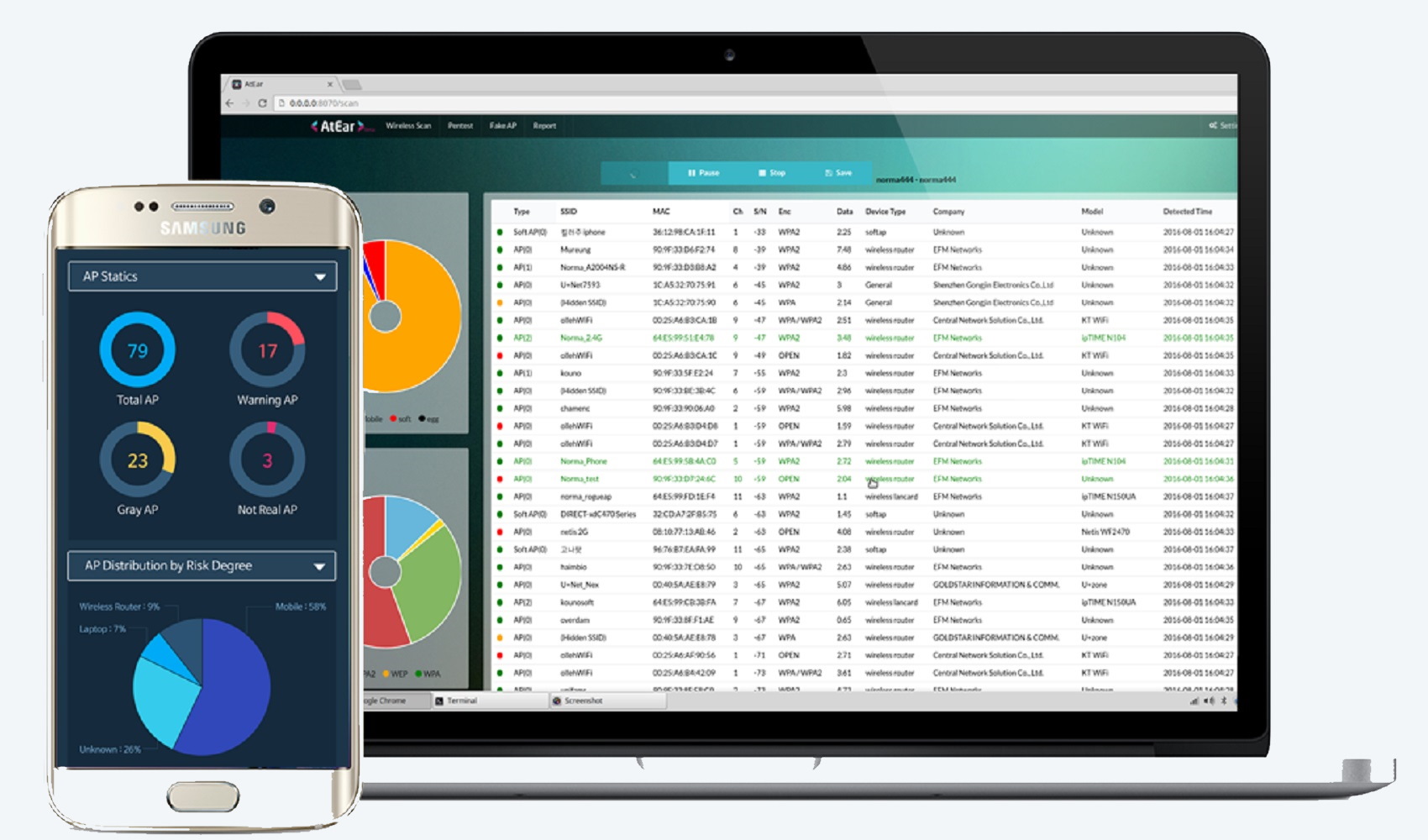
Checking the wireless network status
- Classification of access points and enumeration of connected stations
- Authorized / Unauthorized device classification
Complementing WIPS blind spots
- Manage the general security status of the wireless network in shadow areas where WIPS has limitations to cover
Penetration test
- Testing for Weak Password , Rogue AP, “MITM” and Firmware Vulnerability threats using network penetration testing
Integrated analysis report
- Preparation of a report that incorporates knowledge of wireless verification and wireless network management through the server or the Cloud service
Detection of rogue APs
- Detection and location of unauthorized APs for its removal, one of the most serious problems in wireless security
Customization
- Use of drones to identify the status of a wide network and simulate hacking
- Build up a system of permanent response to security threats based on sensors
Wireless threat detection
- Detection not only of the attack patterns included in the penetration test, but also of new more sophisticated wireless attacks, such as “Fluxion” and “Krack”
Permanent management
- Management of wireless network security continuously through corporate servers or service in Cloud
AtEar, your wireless network security tool
Network Scanning
“Know the status of the wireless network using device classification technology”
—
-
Verify the correlation between AP and devices, and stations, as well as the devices and APs data.
-
Identification of the AP installation status (manufacturer / model, authorized / unauthorized).
-
Device status identification (manufacturer / model, authorized / unauthorized).
-
Check the level of AP risk according to the policies.
Threat Detection
“Detect and analyse wireless attacks”
—
- Verify Wireless Key Weakness, Wireless Denial of Service (“DoS”) Attack, Rogue AP, and “MITM Attack”.
- Detects internally generated wireless network attacks and notifies users.
- In addition, it helps to verify the repetition rate of each attack and analyse the cause.
Penetration Test
“Perform a thorough inspection of the wireless network”
AtEar helps a non-expert to easily carry out expert-level wireless hacking simulation, enabling accurate diagnosis of the wireless network environment.
- Wireless AP firmware version.
- Access Point password security level.
- Internal information leakage by unauthorized AP users.
Report
“Wireless network changes and vulnerability detection history report”
AtEar can create and save a report of collected data, and compare it to the previous verification log, so it allows periodically identify issues and integrate, and analyse many verification points efficiently.


